Evaluating Fuzzers on Cryptographic Protocols
Paper accepted at SBFT 2025 Workshop (co-located with ICSE 2025)
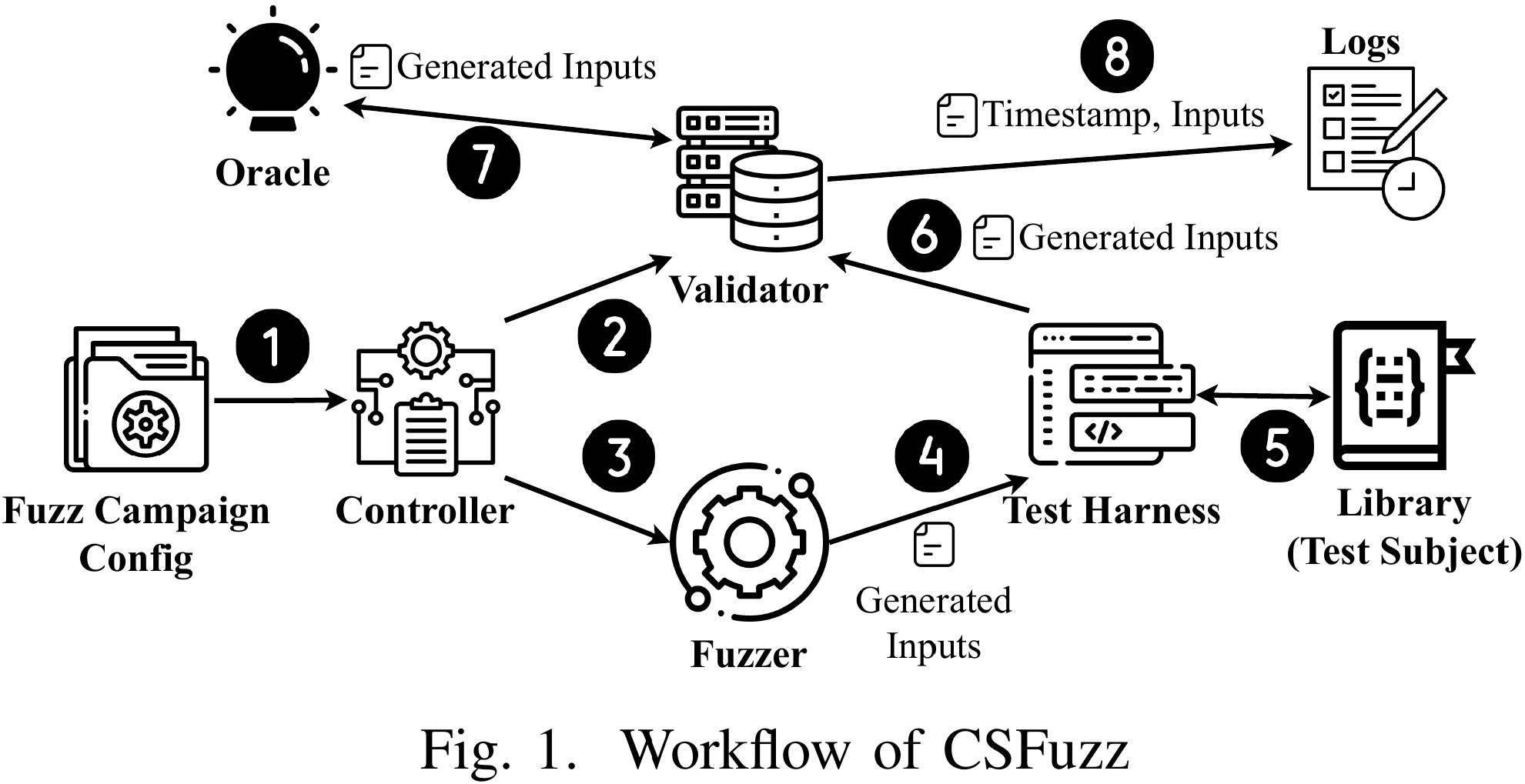
General-purpose fuzzers often struggle to identify vulnerabilities in cryptographic libraries because they cannot generate inputs that satisfy strict protocol validations. This study evaluates modern fuzzers on their ability to produce context-sensitive inputs for PKCS#1-v1.5 signature verification. Our findings show that semantic awareness—understanding complex relationships between input fields—is more critical than code coverage for testing these security-critical implementations.
Paper: FuzzEval: Assessing Fuzzers on Generating Context-Sensitive Inputs
🏆 Submitted as a short paper, it received the Best Paper Award at the SBFT 2025 Workshop, co-located with ICSE 2025.
BibTeX:
@article{hasan2024fuzzeval,
title={FuzzEval: Assessing Fuzzers on Generating Context-Sensitive Inputs},
author={Hasan, S Mahmudul and Kozyreva, Polina and Hoque, Endadul},
journal={arXiv preprint arXiv:2409.12331},
year={2024}
}